John Does
Authorization vs Authentication
Two of the most basic and known concepts in Application Security are Authentication and Authorization.
Applying Authentication informs us who is accessing an application (correct identity); and Authorization informs if someone has access to functionality or resources (determined specific action).
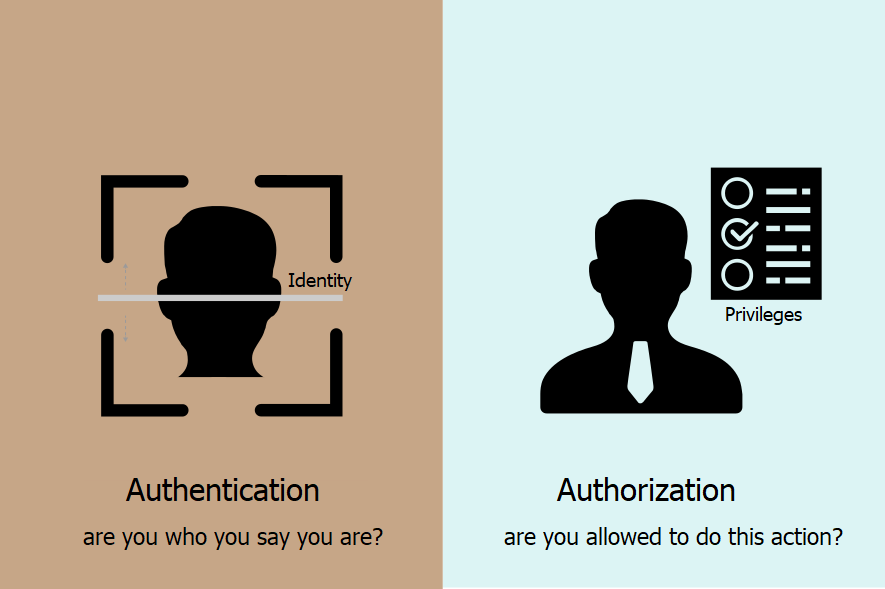
Why Authentication is important?
Any person can go to a public square, but they have to show some credentials to access a private enterprise building.
With an application, it is the same. A user has to be identified, usually by informing a username and password. In this way, the user can be tracked along with the application for process, update or query any information. In some companies, tracking is essential for auditing compliance.
Why Authorization is important?
A person may be invited for a meeting in a company, but it doesn't mean that it's allowed to enter in the accounting room.
It's how authorization works in applications. Not all the persons have access to all functionalities of an application. For example, a user can have access to his salary, but only the manager can see the salaries of the members of the team. In fact, users only should have the necessary access to do their job, and thus it's what is called Principle of Least Privilege. In the same way of authentication, having a tracking of what each operation each user executed it's very important when auditing is a requirement.
Working with Authentication
There are many rules for authentication such as password length and hashing algorithms and this shouldn't be in control of the applications. Custom code is hard to maintain updated against company policies, can have security bugs and probably there will be duplicated code along with company applications.
Companies have external entities like Identity Management and LDAP servers which are responsible for authentication, known as Single Sign-On. For example:
- Microsoft ADFS
- Oracle Identity and Access Management
- Amazon Cognito
The applications authenticate the users against these entities using the standard protocols like SAML, oAuth or OpenID (these will be discussed in a future article).
Authentication Techniques
The way users or applications authenticate themselves depend on requirements and the device they are using. These are the most common authentication techniques:
- Basic: The user and password are informed through the transport layer in Base64 encoding. For example, when informed through a URL using the credentials test/password, it could be:
- http://dGVzdDpwYXNzd29yZA==@www.example.com
where dGVzdDpwYXNzd29yZA== is converted to ASCII as test:password
This communication should be done through HTTPS
- http://dGVzdDpwYXNzd29yZA==@www.example.com
- Form-based: Essentially the idea is similar to Basic, but the user informs the credentials using a form in a web page. Communication should also be secured through HTTPS.
- Client-cert: The client authenticates itself using a digital certificate. It's more secure than the previous mechanisms, but it requires the client have a certificate and currently the process for it it's not smooth once the person has to present ID document to a Certificate Authority (CA) in order to emit the certificate. Keep in mind that the certificate has potentially the same value as a person ID.
Besides this process, the other reason that people don't have a certificate it's because there is a cost associated with them when a CA emit it. Because of that, the most common usage is inside companies, where they are responsible to generate a digital certificate for employees or mainly for machines so that a server can trust another server through a Client-cert authentication.
- Mutual Authentication: Also known as two-way SSL, it is normally used between servers communication. The client uses a digital certificate to authenticate itself in another server, as explained in Client-cert authentication, but the authentication also occurs in the opposite way through its server certificate.
- Passwordless Authentication: The user is verified through One-time Password (OTP). A code is sent to the user's phone or e-mail whenever it's necessary an authentication.
- 2FA/MFA: Two-factor Authentication (2FA) or Multi-factor Authentication (MFA) refers to two or more security authentication levels. For example, after the user informs the password, an OTP is sent to the e-mail, so it has to be informed in a second step.
- Single Sign-on (SSO): It allows users to access multiples application with a unique login.
- Social Authentication: It authenticates users through social network platforms such as Facebook or LinkedIn.
Federated Authentication
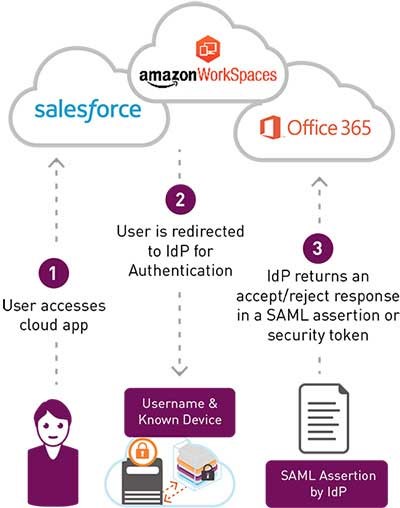
As it was commented above, companies usually have entities responsible for keeping the user storage and control the identity access and management, usually referred to as Identity Provider (IDP).
So instead of the application authenticates the users using a custom mechanism, it delegates the authentication, usually trough a configuration, to an IDP. So, in the first time user enters in the application, it's redirected to the IDP, which presents a login page. After the IDP authenticates the user successfully, returns a valid token, such as SAML, and the user it's redirected back to the application, which keeps the user authenticated for a time.
Working with Authorization
Usually, authorization is checked against user responsibilities, but an application can allow or deny access based on other elements such as an hour of the day or geographic position.
In applications, an anonymous user won't have access to any enterprise resources, so authorization really takes place after the user is authenticated.
Focusing on enterprise applications, the user is authenticated against Identity Provider, and in this context, there are two approaches:
- The Identity Provider authenticates the user but blocks the access to the required resources based on configured roles.
- The Identity Provider returns the user attributes and groups from LDAP after authentication.
While in the first approach it is required some configurations on IDP side, in the second one the responsibility stays with the application side, where the user's groups and attributes are checked used to create a rule.
In the application side the better option it is to configure any authorization rule using the infrastructure supporting the application, like the application server or the platform. Usually, these configurations are declarative, which implies a clear configuration and easy maintenance. When it's not possible to configure authorization in a declarative way, the alternative it is to insert conditions in the code, what it resolves the problem, but implies in hard maintenance.
Authorization Techniques
These are the most common authorization techniques:
- Role-based access controls (RBAC): It's a method of restricting access based on the roles of individual users within an enterprise.
- JSON web token (JWT): It's an open standard for securing data transmitted between parties.
- Saml Assertion Markup Language (SAML): It's standard for Single Sign-on.
- OpenID authorization: It verifies user identity based on an authorization server’s authentication.
- OAuth: It allows the API to authenticate and access the requested system or resource.
Advantages of Single Sign-on
Some advantages of SSO:
- Reduces password fatigue. Remembering one password instead of many makes users’ lives easier. As a tangential benefit, it gives user greater incentive to come up with strong passwords.
- Simplifies username and password management. When changes of personnel take place, SSO reduces both IT effort and opportunities for mistakes. Employees leaving the organization relinquish their login privileges.
- Improves identity protection. With SSO, companies can strengthen identity security with techniques such as two-factor authentication (2FA) and multifactor authentication (MFA).
- Increases speed where it is most needed. When large numbers of people and departments demand rapid and unfettered access to the same applications, SSO is especially helpful. In such cases, preventing errors and malware intrusion can be the difference between life and death.
- Relieves help desk workloads. Fewer users calling for help with lost passwords saves money and improves security.
- Reduces security risks for your customers, vendors, and partner entities. Connections between allied companies always present vulnerabilities, which SSO can reduce.
References
https://www.okta.com/identity-101/authentication-vs-authorization/
https://dis-blog.thalesgroup.com/security/2017/08/29/identity-provider-idp-need-one/
