Playing it safe
Keeping our websites safe
Protecting our websites from injection which is considered the most common and most dangerous vulnerabilities.

We live in a technological world where most things are connected through the Internet. Smart-cars-houses-devices-watches are beyond their basic capabilities and in constant evolution. Websites are also a good example of innovation because, in the past, they were merely texts/images on an HTML page. We may say, it was created for fun and entertainment, but now we use it for shopping, banking, advertising, etc. Today, it connects humans and companies globally and that’s why we need to keep it secure. The boundaries between our real world and the digital world are thinner than ever and threats are constantly appearing, sounds apocalyptic, doesn't it?
In order keep our websites secure, we have created 10 tips based on the OWASP Top 10. The Open Web Application Security Project (OWASP) is a nonprofit foundation that works to help and improve the security of software by proving guidelines and best practices for it. According to OWASP Top 10, the most common and dangerous vulnerability is Injection, because it’s a very broad category that includes practically most of all serious web application security risks.
Injection
Injection flaws occur when an attacker can send hostile data to a web service, API, etc., and it gets executed it can result in data loss, corruption, or disclosure to unauthorised parties, loss of accountability, or denial of access. We have different kinds of injections, such as SQL Injection, OS Command Injection, XPATH, LDAP Injection. In this article, we’ll focus on SQL Injection, because it’s a type of injection that might cover all the other types due to the way of operation.
SQL Injection is dangerous because it uses true mechanisms for sending/querying information, but maliciously, and that’s why that the infrastructure’s control does not block it. It believes that the user is doing an acceptable query but, he’s using it for malicious purpose.
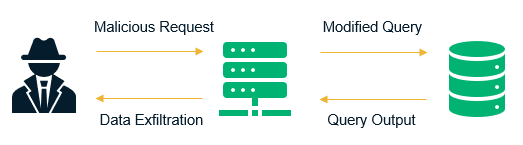
How does the attack work?
In the example below, we can see a real attack to an open-source streaming platform called YouPHPTube and AVideo that could lead to remote code execution. This vulnerability was discovered this year and it was already sent to the owners of the project.
Basically, this vulnerability happened because it wasn't properly sanitize user input data $_GET['catName']. The only security control focus on checking and removing simple quotes in the user’s given strings. With this vulnerability, an unauthenticated user is able to retrieve MySQL error messages by using an encoded “\” -> %5c.
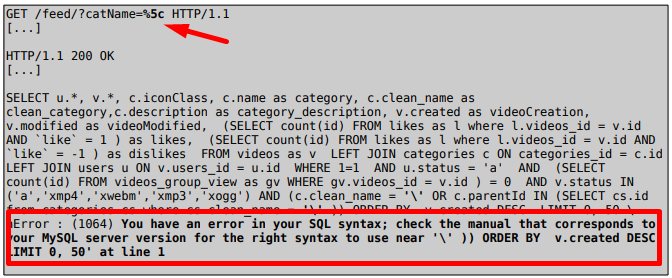
Figure 2 - Using an encoded “\”, it was possible to receive an error message. Now that we know it’s possible to bypass filter using encoding, it’s possible to retrieve, for example, the passwords from table users using a UNION query and encoded characters %23 (‘) and %5c (\) at the end.

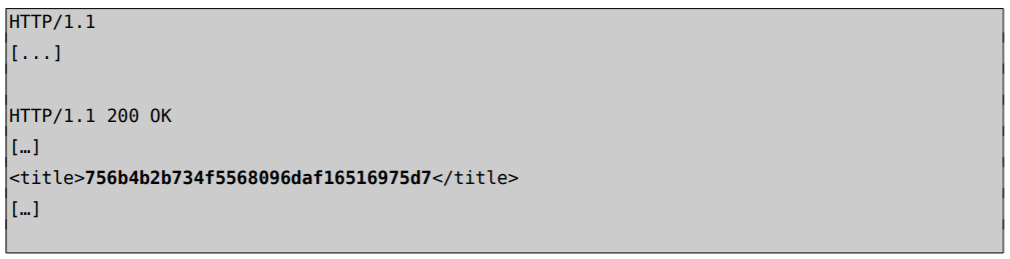
The link for the complete POC can be found here and link the news regarding the vulnerability can be found here.
How can we protect ourselves?
With the user input being the main attack vector, the best approach is controlling and even blocking user input based on specific patterns. Developers can also avoid this threat by applying the following techniques:
- Prepared Statements (with Parameterized Queries): ensure that an attacker is not able to change the intent of a query, even if SQL commands are inserted by an attacker;
- Stored Procedures: Stored procedures are used to group one or more SQL statements, so whenever you need to execute a query you just execute it, also it can be stored for later and used many times;
- Limiting Privileges: Be careful, do not connect your application to the DB using an account with root access. It’s recommended to enforce the least privilege to defend the application against SQL Injection;
- Keeping database credentials separate and encrypted: It’s important to keep credentials to the Database encrypted and inside a “vault”. In case of a successful attack, they won’t be able to “decipher” the key to access it;
- Input Validation: Perform proper input validation using a regular expression as whitelists. The validation process is aimed at verifying whether or not the type of input submitted by a user is allowed.
SQL Injection is one of the most common vulnerabilities according to OWASP due to improper input validations and poor implementation of protection mechanisms. Injection can result in large data loss, public disclosure by attackers, denial of service, among others. As we read above, it is quite simple to solve it. It must be considered seriously by developers since the planning phase of a project when using a database. Besides that, there’re some frameworks such as Hibernate (HQL) to help to construct queries more securely (if teams implement it correctly and maintain it up to date). To conclude, it’s highly important to protect our applications from SQL Injection by using code defensively and monitoring crucial environments.
Read the full article, here.
